Imagine that you are a Russian or American general officer responsible for the safety and security of 6-7,000 nuclear warheads—enough to kill hundreds of millions of people. Most are likely stored in bunkers protected by thousands of troops and associated comprehensive security systems. Hundreds may be in trucks or railcars on their way from one site to another accompanied by security teams trained to quell an attack or respond to an incident during transit. All the sites and all the movements are conducted in secret and information is carefully controlled to make sure even your guard forces don’t have any more information than they need for their jobs.
The system is safe and secure, but suddenly, out of the blue, the media has picked up a story based on an anonymous twitter account that’s reporting a nuclear warhead has gone missing during a transit shipment and the truck driver is unaccounted for. Or maybe a hacker group has claimed to have access to your inventory management system and any information you provide can’t be trusted. You might consider ignoring the report or simply issuing a statement that all weapons are accounted for, but you know that won’t be the end of it. As the senior official responsible for managing the warheads of a nuclear weapon state, you will need to demonstrate your authority and capability or risk enabling your enemies to exploit any vulnerability or gap in your inventory data and control. How do you verify or debunk the reports and assure the world community that all of your warheads are secure and safely in your custody?
The only way you could possibly respond with any credibility is if you have the most reliable and secure inventory management system in the world and you can track and account for every one of those thousands of warheads and components at every moment in time. It has to be so secure that it can’t be penetrated without detection by the most capable cyber-hackers from America, Russia, China, or any other country or organization. The system has to be on the most secure networks in the world and have so many redundant system checks that you can detect even the most skilled and stealth hackers. It also has to be so reliable that you can identify every person, every component, every movement, every step in the supply chain, and every location in real-time and you can trust the data in your system with your life. Your system has to be 100% fail-safe, just one glitch or flaw could provide an opening for a loose nuclear warhead that could destroy a city, — and you have no margin for error.
Inventory Management Cooperation with Russia
Now, let’s travel back in time to the early 1990s when Russia inherited the nuclear warhead stockpile amassed by the Soviet Union. At that time, unclassified estimates of the warhead stockpile in 1990 was approximately 40,000, and those warheads were not only in Russia, but also in storage sites in Ukraine, Belarus, and Kazakhstan. When Cooperative Threat Reduction (CTR) programs initiated technical talks in 1992 and 1993, nuclear security concerns were at the forefront, but the issues and details associated with the warhead inventory were still so sensitive that it was difficult to identify the initial steps and the first projects that the sides could agree to pursue. The first offer of assistance that the Russians agreed to was the provision of armored blankets to be placed over warheads as they were loaded on trains and shipped from Ukraine, Belarus, and Kazakhstan to Russia for safe keeping.
It wasn’t until April 1995 that CTR implementing agreements on Nuclear Weapons Storage and Transportation Security were signed that technical talks began directly with the Russian Ministry of Defense’s (MOD) 12th Main Directorate (12th GUMO) that is responsible for the management and security of the Russian nuclear warhead stockpile. The first project was relatively straight forward to address during initial technical talks. CTR purchased 50km of triple-layered security fencing with microwave sensors and fence disturbance systems. The 12th GUMO approached technical talks with some understandable trepidation and skepticism regarding American goals and objectives for the program, so the first step was limited to CTR nuclear security equipment procurements. The 12th GUMO was not ready for Americans to share information on the nuclear warhead sites and nuclear security capabilities at first, so they assumed full responsibility to ship those systems to the sites and install them.
Soon after the first equipment deliveries were delivered and the full provision of physical security equipment was underway, CTR nuclear security technical talks turned to the critical, but extremely sensitive, topic of inventory management. Russian and American experts knew that a more comprehensive nuclear security cooperative program would need to be formulated around a strong, central inventory management and control system for the Russians to credibly demonstrate their critical control capabilities tracking their stockpile of nuclear warheads. It was not clear how the Russian nuclear warhead inventory was being tracked and monitored at the time.
Technical talks on inventory management began with tentative information sharing. The 12th GUMO described its system for inventory management based on secure communications lines which consisted primarily of data inputs that were faxed and transmitted to 12th GUMO headquarters from the storage sites. There was no central, automated inventory management system for all those warheads. The stockpile information was secure, but updates were not available until operations and shipments were complete, and as a result it was practically impossible to consolidate data on the entire inventory in real time. The 12th GUMO estimated that the process to conduct a 100% audit of the warhead inventory would take two to three weeks. Unlike fissile material accounting that requires more extensive analysis to provide precise measurements of material within processing operations, accounting for units like warheads, each of which poses tremendous explosive capability, should be possible within hours or days at the most.
The 12th GUMO expressed interest in cooperation to improve their inventory management system, but lacking a strong domestic computer hardware and software industry, the Russian inventory management specialists were not very familiar with the available technology and were not confident that such technology could be safely and securely used to manage their nuclear warhead inventory. They didn’t know if they could trust any Western technology to protect the most sensitive assets in the Russian military.
As a first step, the CTR nuclear security team proposed a technical demonstration. The demonstration turned out to be a key milestone in the program. It was conducted in Moscow in 1995, soon after the first nuclear security agreements were finalized with the 12th GUMO. The demonstration involved development of a dummy database developed by the CTR experts based on unclassified historical data on Russian warhead sites and uploaded to an Oracle-based system with a series of computers set up to re-create a virtual control center and multiple remote terminals such as would be installed at Russian nuclear warhead storage sites.
While developing the demonstration, the CTR team consulted with the DTRA experts responsible for managing the American nuclear warhead inventory management system that was called SWIM for “Special Weapons Inventory Management System.” The demonstration showed all typical warhead transactions, including: how shipments were tracked to and from facilities; how transfer of custody documents were handled; how locations were tracked, including a demonstration of data transfers between simulated sites; how the system tracked personnel involved in transactions; how system reliability was maintained; and how total inventory audits were conducted. The concept was to provide the 12th GUMO with the computer hardware and application software that the 12th GUMO would use to design the specifics of their database and load data once the system was operational.
After the demonstration, the 12th GUMO’s interest in developing a program to develop such capabilities with U.S. support grew, and technical talks intensified.
Two major obstacles stood in the way of providing the 12th GUMO with a centralized, Automated Inventory Control and Management System (AICMS). Russian technical experts needed to be sure that the software would be free of any bugs or backdoors that could be exploited by the West to track Russian warheads, and the facilities needed to be protected from potential electronic eavesdropping. The CTR program took a couple of extra-ordinary steps to demonstrate that its goals and objectives were sincere.
First, CTR technical experts approached Oracle to find a way to reassure Russian experts that the software was clean. Weeks of talks with Oracle finally led to an agreement whereby the Russians were allowed to send their best software experts to examine the Oracle software code in their clean room at their Headquarters in Silicon Valley. CTR paid for the Russian experts to fly to California where they were given full access to the software codes in clean rooms, but they could not have any electronics or even paper or pen with them during the examination.
Second, CTR agreed to provide extensive electronic shielding of the servers that the 12th GUMO would use at its AICMS sites. In order to protect against anyone seeking to use remote electronic means to intercept emanations from the facilities, CTR provided shielding material that was installed within the walls surrounding the server rooms. US export laws prevented sharing classified standards or capabilities, so the shielding material was the most effective commercial product available at the time. Essentially, CTR agreed to provide capabilities to protect against electronic surveillance and intrusion roughly equivalent to secret compartmentalized information facility (SCIF) requirements so that the Russians could counter anyone attempting to steal electronic data on the Russian warhead inventory. These two agreements went a long way toward generating trust between the 12th GUMO and CTR project teams, and were a key aspect of the cooperation that led to the AICMS program and many of the subsequent nuclear security cooperation programs that followed.
In order to verify these two agreements, CTR agreed to support the Russian MOD who performed system “attestation” at each facility prior to operations. Attestation is a mechanism for software to prove its identity. The goal of attestation is to prove to a remote party that your operating system and application software are intact and trustworthy. Russian MOD certified all hardware and software provided, including x-ray examination of hardware and code-level review of software. Oracle software also included an identify manager function that allowed the Russian system administrators to validate user processes.
With those two agreements in place, the program quickly expanded and accelerated. In November 2001, Gen. Lt. Verhovtsev, Chief of the 12th GUMO, reported that meetings were held with President Putin and that he expressed his personal support for the program.
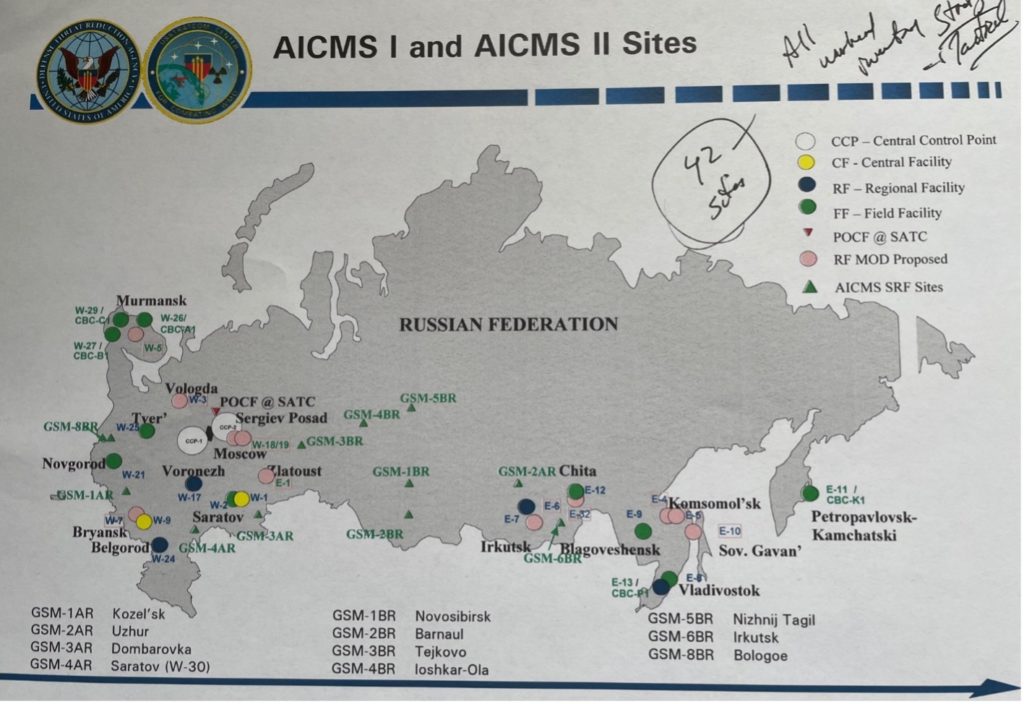
In addition to supplying the computers, servers, electronic equipment, and the software, the program included the design, development, and provision of AICMS facilities (small, modular buildings) that were installed at various storage sites (Figure 1 below)

The Scope and Coverage of the AICMS System
The AICMS project was executed in 3 phases, roughly corresponding to the sites supported. Phases I and II covered the 12th GUMO bases, Phase I (2000-2005) included 18 sites; Phase II provided 13 additional sites: Murmansk; Vologda; Vyritsa; Bryansk; 2 sites near Moscow; Volgograd, Zlatoust; Irkutsk; Chita; 2 sites at Komsolmosk-na-amure; and Sovetskaya Gavan. Phase I and II locations were determined by MOD requirements to locate facilities within storage sites requiring reporting, and in some cases only one AICMS facility was provided to serve more than one nearby facility.
Phase III expanded the network to include nuclear warhead storage bunkers at SRF sites. Office of the Secretary of Defense Policy approval required extensive analyses to provide assurances that AICMS facilities at these bunkers at Strategic Rocket Forces (SRF) sites would not contribute to managing the deployed warheads. MOD provided assurances that warheads at these sites were under control of the 12th GUMO and not included in SRF deployed arsenal. When the AICMS program began, the program was initially focused only on managing warheads “destined for dismantlement,” but with this expansion to include bunkers at SRF sites, the scope of the program essentially included all non-deployed warheads in the custody of the 12th GUMO. This expansion required a high level of trust in the 12th GUMO’s purpose and intention for use of the AICMS system and would not have been possible without years of technical discussions and access provided to the CTR teams.
During Phase III there were eleven (11) AICMS SRF sites added including: Kozelsk; Uzhur; Dombarovka; Saratov; Novosibirsk; Barnaul; Tejkovo; Ioshkor-Ola; Nizhni-Tagil; Irkutsk; and Bologoe. These additional nodes were located at SRF bases that included the deployed nuclear weapons, but the nodes were located in the secure areas within the base that contained the storage bunkers and AICMS node under the custody of the 12th GUMO. The intent was for this system to manage all non-deployed warheads. These nodes were added in a different phase because the Department of Energy (DOE), and not my team at DOD, was responsible for security upgrades at these sites. Phase III cost was $30M, total system cost for CTR was approx. $115M.
In addition to providing AICMS facilities at nuclear warhead storage sites, CTR provided a Command and Control facility in downtown Moscow near MOD headquarters equipped with similar SCIF-like characteristics. This facility housed the network servers and workstations for the 12th GUMO AICMS team to manage the overall AICMS inventory. CTR confirmed completion of the construction, but was not allowed inside the facility once construction was complete. CTR also provided a second Command and Control facility, designed as a back-up, near Sergiev Posad north of Moscow. (Figure 2 below)
Extensive Technical Discussions on Inventory Management
Technical discussions on inventory management were a major core of CTR nuclear security cooperation from the initial talks in 1995 through the expiration of the CTR agreement with Russia in 2013. These exchanges with the 12th GUMO AICMS team included discussions with the CTR project technical experts as well as with the Defense Threat Reduction Agency (DTRA) inventory management office that managed the SWIM system as well as its next generation follow-on, the Defense Integration and Management of Nuclear Data Services (DIAMONDS) system.
At first glance, it may seem that developing a warhead inventory management system would be a fairly straight-forward task, simply involving a serial number for the warhead and a system to track its location. In fact, however, the effort becomes enormously complex as you understand the many components, the numerous locations, the operational status of the warheads, the requirements for regular security checks, the age and condition of all components, the personnel with access to the warheads and with access to the inventory management system, the security and reliability checks within the systems, and the frequent operations and maintenance functions required for the safety and security of the warheads.
Before developing the AICMS system, the 12th GUMO technical experts relied on a system that used paper “passports” that accompanied the warhead everywhere it went. Warhead passports contained records of every transaction, every component, and every action that impacted the warhead throughout its service life. From the first transfer of custody from Rosatom to the 12th GUMO to the final return to Rosatom, every action taken with regard to that warhead was recorded on the paper passport. AICMS automated this system and provided a real time capability to gather and consolidate the data for the entire stockpile. While the DTRA inventory management systems SWIM and DIAMONDS did not define passports associated with each warhead, they did capture all of that same kind of information and data. Russians went so far as to track and monitor shipping and storage containers as independent elements in their AICMS system because they understood that the loss of such components could be used by terrorists to simulate or represent a warhead if the 12th GUMO were to lose custody of any of these containers.
The 12th GUMO’s procedure was to record all actions for each warhead on site, by hand and on paper, then bring the record to the AICMS facility to be recorded electronically and reported back to the command center. The database tracked every action and every time anyone had access to each warhead, essentially recreating the paper passport that always accompanies each warhead. All maintenance actions were to be captured, including every person with access, actions taken, dates and times – including every security check.
The AICMS system was designed based on the principals of Confidentiality; Integrity; Availability; and Accountability (CIAA) – each of which were reviewed and discussed between the parties during intensive, detailed technical exchanges. The database and software requirements were jointly developed over the course of years of technical discussions. The inventory database accounted for all storage sites and rail transfer points. The AICMS system provided modular buildings with workstations as pictured in the figure. Software designed to certify and monitor every key stroke made on the system, assigning authorized codes for all data updates with certified date/time stamps. The AICMS system included secure communications and encryption provided by MOD; data protection, system security, and use accountability provided by the application software; as well as facility shielding provided by CTR. AICMS preserves the integrity of data at all echelons, capable of local and centralized recovery of data and redundant communications links. The AICMS functionality includes entering, changing, reporting, auditing, and archiving, thus supporting changes in inventory status and chain of custody for the nuclear warhead inventory. The system can monitor history of operations and monitor movements in real time. It allows decentralized data entry and update with on-demand local and remote access.
After years of technical discussions between our experts, the 12th GUMO noted that the AICMS system was capable of conducting a comprehensive audit of the entire inventory of nuclear warheads within a couple of hours – a huge improvement in capability from the original estimate of several weeks. At the time, estimated database workload requirements were estimated at 1 transaction per minute.
Applications of Inventory Management Technical Exchanges Today
Understanding the detailed technical exchanges conducted between the United States and Russia on inventory management provide insight into how to address current nuclear security challenges.
The exchanges between DTRA technical experts and the 12th GUMO demonstrate the utility of continued technical exchanges. We know that the AICMS and DIAMONDS systems were developed in parallel, with common functions by experts with shared goals and objectives. The AICMS and DIAMONDS systems are quite similar in design and function, tracking all warheads in the active, reserve, and dismantlement queue. Both systems were developed using an Oracle assurance system for data validation, access, and system administration. Both systems rely heavily on tracking every user on the system and protecting and verifying appropriate access.
We also know that such discussions were conducted despite the extreme sensitivities of the data that the systems are responsible for managing. Technical discussions were conducted on design and functionality without requiring the sharing of information that both sides consider among the most sensitive in the world, such as production and dismantlement schedules, current operational data, serial numbers, and even passcodes. As a core nuclear security function, future technical exchanges on capabilities and functionality of inventory management systems for nuclear warheads could serve as a potential area for cooperation.
Given growing concerns between the United States and Russia on cybersecurity issues and hacking incidents, technical exchanges on nuclear warhead inventory management could offer a positive area of cooperation between the two countries. The United States and Russia worked together on the AICMS program to design and implement hardware, software, and facility enhancements to provide protection against potential hackers. Both countries agreed that warhead inventory management systems ought to be provided with the highest possible level of protection – even going so far as to protect against each other’s capabilities. Such exchanges could enhance common nuclear warhead security objectives and could lead to a potential agreement to refrain from any actions that could impact on inventory management. Further, this cooperation could provide a foundation for future agreements to enhance protections of other critical electronic infrastructure such as Command Control and Communications systems that neither party would want to be vulnerable to attacks from any party.
This is also an area of mutual interest that has overlap with arms control. If the United States and Russia were willing to consider an agreement to share data on nuclear warhead inventories, or perhaps to agree on warhead limitations, the mutual experience of our AICMS and DIAMONDS technical teams could provide a strong basis for technical negotiations. We understand how each of our inventory management systems work and we know that technical data exchanges would have to be derived from the way those systems work, the data that they track, and how they track that data. If there were to be an agreement on nuclear warhead limitations, it would have to account for warhead passport data to uniquely identify individual warheads if they were to be tracked.
Perhaps the most important consideration when looking back at these inventory management exchanges is the knowledge and confidence that each side should have on the capabilities of the other side to track and manage its current nuclear warhead stockpile. We should be confident in each sides’ ability to respond to the opening scenario involving a rogue report of a problem associated with warhead inventory data or reports of a missing warhead. The countries have the ability to confirm and present evidence showing that all warheads are thoroughly tracked in real time.



